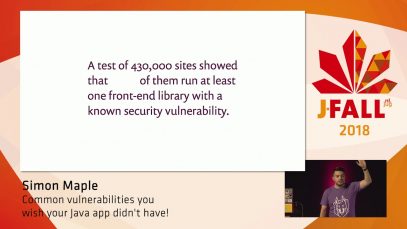
J-Fall 2018: Maarten Mulders – SSL/TLS for Mortals
Using Transport Layer Security (TLS) the right way is often a big hurdle for developers. We prefer to have that one colleague perform “something with certificates”, because he/she knows how that works. But what if “that one colleague” is enjoying vacation and something goes wrong with the certificates? In this session we’ll take a close […]