J-Spring Digital: Brian Vermeer – Know thy neighbours: dependency management done right
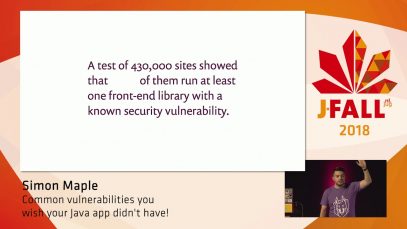
We all love scaffolders like Spring Boot Initialzr. It creates a brand new app with all the latest versions of the libraries we need to get going, enabling us to build awesome applications quickly. But after creating our initial application who is responsible for the dependency management and what happens over time when new features […]